According to the Palo Alto Networks threat report,[1]Palo Alto Networks, “2020 Unit 42 IoT Threat Report,” https://unit42.paloaltonetworks.com/iot-threat-report-2020/ 98 percent of IoT (Internet of Things) device traffic is unencrypted, exposing personal data on hospital networks. In addition, 72 percent of healthcare Virtual Local Area Networks (VLANs) mix IoT and IT assets, allowing malware to spread from computers to vulnerable IoT devices on the same network. These vulnerabilities allow hackers to access network traffic and collect confidential information, then exploit that data for profit on the Dark Web or alter data to cause harm.

Major cyberattacks, aimed at either disrupting or extorting a system, have always targeted significant entities such as power grids, supervisory control and data acquisition (SCADA) system architecture, and healthcare systems. Manufacturing and healthcare systems are so susceptible that they will suffer 74 percent of all attacks by 2025, according to the Palo Alto report. Also, vendors’ and manufacturers’ software can be compromised and allow hackers to access devices, such as an insulin drip.[2]Joyia, G. J., Liaqat, R. M., Farooq, A., & Rehman, S. (2017). “Internet of medical things (IoMT): Applications, benefits and future challenges in healthcare domain.” J. Commun., 12(4), … Continue reading
In recent years, ransomware attacks on hospitals have increased, including the famous WannaCry hack aimed at hospital CCTV cameras. Malicious users block authenticated users from access to their files and hold the data hostage until a ransom is paid. Countermeasures are important to protect system files and promote computer hygiene, such as up-to-date antivirus software, data back-up (preferably on an external or offsite drive), disabling unused ports and applying any security patches for the operating system such as Windows.[3]Zou, Y., Roundy, K., Tamersoy, A., Shintre, S., Roturier, J., & Schaub, F. (2020, April), “Examining the adoption and abandonment of security, privacy, and identity theft protection … Continue reading Regardless of the attack sources—criminal organizations, nation states or script kiddies—cyberwarfare is tremendously harmful. Exfiltrated patient data can be used for identity theft and other forms of fraud. Stealing confidential patient information contributes significantly to the ongoing rise in identity fraud nationwide.[4]Humayun, M., Jhanjhi, N. Z., Alsayat, A., & Ponnusamy, V. (2021). “Internet of things and ransomware: Evolution, mitigation and prevention,” Egyptian Informatics Journal, 22(1), 105-117.
Worse, patient information can be altered—or deleted—regarding treatment and drug names and dosages, with potentially catastrophic results. Patients can suffer severe injury or even die if a hacker gains unauthorized access to monitoring or other medical equipment and outputs false data. Similarly, devices administering medicine, such as infusion and insulin pumps, can be shut off or dosages wrongly increased by hackers. Imagine the potential harm if a hospital’s power, including backup generators, is turned off. Monitoring screens go blank, or cardiac devices are compromised, or access to the blood supply is blocked during major surgery, such as a double transplant.
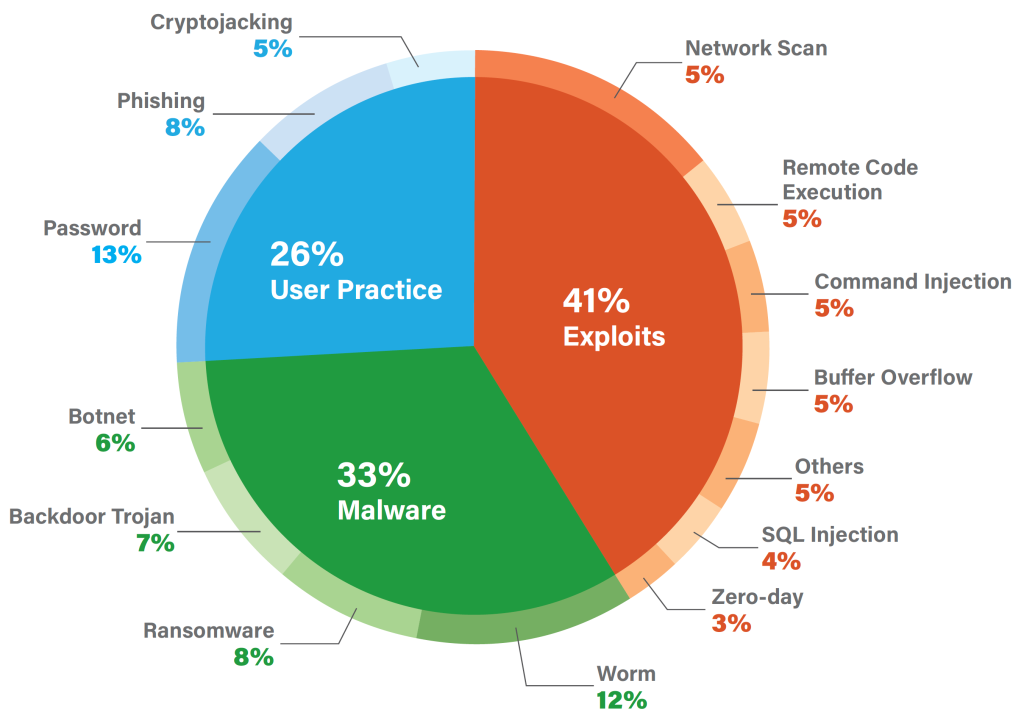
In the graph above, non-secure IoT devices account for about half of reported cyber-exploits in all industries.
User online practices represent 26 percent of all threats. Half of these concern password issues, followed by phishing and cryptojacking. Malware accounts for a third of threats, shared by worm attacks at 12 percent and almost equally by ransomware, backdoor trojans and botnets at 6, 7 and 8 percent, respectively. The largest proportion of threats involve exploits at 41 percent, with network scans at 14 percent; remote code execution, command injection, buffer overflow and miscellaneous attacks at 5 percent each; SQL injection at 4 percent; and Zero-Day attacks at 3 percent.
Based on the report, when security measures such as patches, updates, password and asset management policies are continuously implemented, user-level threats would decrease from 26 to 13 percent, malware threats from 33 to 13 percent, and exploits from 41 to 27 percent.
Cybersecurity in healthcare needs an urgent upgrade, especially since medical devices can be hacked without any indication. Information protection should not become important only after a data breach but throughout the security design that houses both highly secured connections and IoT devices, which are not highly secured connections. When organizations fail to upgrade security due to budget restraints, they might have to pay a hefty ransom to have the malware flushed out of their systems and their data released.
Vulnerability
Ransomware attacks have increased tremendously since their first detection in 1989.[5]Leo, P., Isik, Ö., & Muhly, F. (2022). “The Ransomware Dilemma,” MIT Sloan Management Review, 63(4), 13-15. The cost of ransomware attacks has skyrocketed from $10 to $210 billion from 2015 to 2021, which illustrates the importance of securing IoT devices.[6]Keary, J. (2022), “Rebuffing Russian Ransomware: How the United States Should Use the Colonial Pipeline and JBS USA Hackings as a Defense Guide for Ransomware,” Seton Hall University Law Library, … Continue reading Examples of ransomware targets in 2021 include Kaseya, an IT management and security software company, ($70 million in Bitcoin),[7]Mohurle, S., & Patil, M. (2017), “A brief study of wannacry threat: Ransomware attack 2017,” International Journal of Advanced Research in Computer Science, 8(5), 1938-1940. and JBS USA Holdings, Inc., a food processing company, ($11 million in Bitcoin).[8]Bunge, J., “JBS Paid $11 Million to Resolve Ransomware Attack,” Wall Street Journal, June 9, 2021.
Both Kaseya and JBS were hacked by REvil, a Russian cybercriminal organization, which attacked more than 360 American targets in 2021. REvil then leveraged Kaseya’s “connectivity to the larger internet ecosystem to infect more than 1,500 organizations around the world.”[9]Collier, K., “Major Russian-speaking ransomware gag behind JBS and Kaseya attacks goes offline,” NBC News, … Continue reading
Among the major areas where IoT devices are primarily targeted, the healthcare industry leads the way at 41 percent of attacks, as shown in the graph below, because of the ease with which medical devices can be penetrated.[10]Yaqoob, I., Ahmed, E., ur Rehman, M. H., Ahmed, A. I. A., Al-garadi, M. A., Imran, M., & Guizani, M. (2017), “The rise of ransomware and emerging security challenges in the Internet of … Continue reading The tremendous growth of the internet has made device accessibility more prolific. Imaging devices alone account for 51 percent of threats to healthcare organizations. As a result, there have been many high-profile breaches that amplified the need for robust cybersecurity measures to combat ransomware attacks.
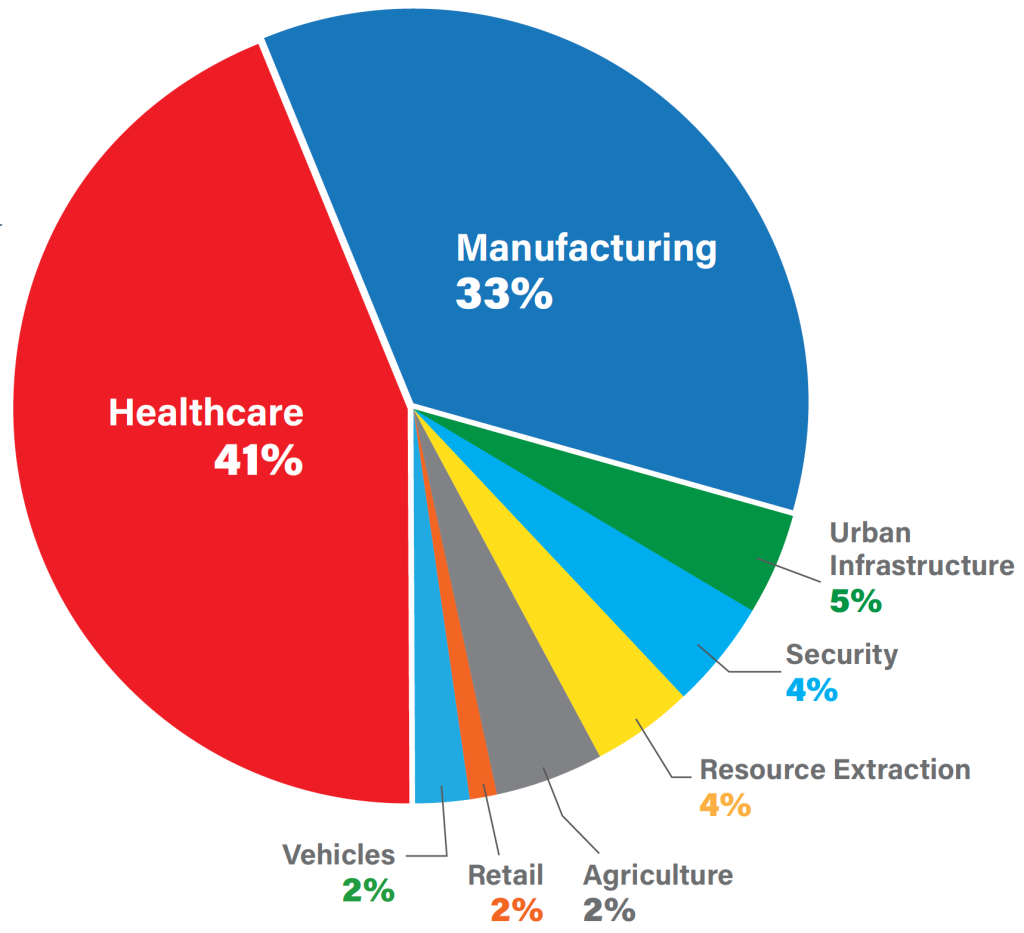
Malicious network and Denial of Service (DoS) attacks are the most dangerous. Today’s doctors and nurses must stay connected to various medical devices in real-time since these machines are integral to diagnosis and treatment.[11]Hassija, V., Chamola, V., Bajpai, B. C., & Zeadally, S. (2021). “Security issues in implantable medic al devices: Fact or fiction?” Sustainable Cities and Society, 66, 102552 An additional area of concern involves vendors and manufacturers whose software can be compromised, which might allow hackers access to medical devices.[12]Joyia, G. J., Liaqat, R. M., Farooq, A., & Rehman, S. (2017). “Internet of medical things (IoMT): Applications, benefits and future challenges in healthcare domain.” J. Commun., 12(4), … Continue reading
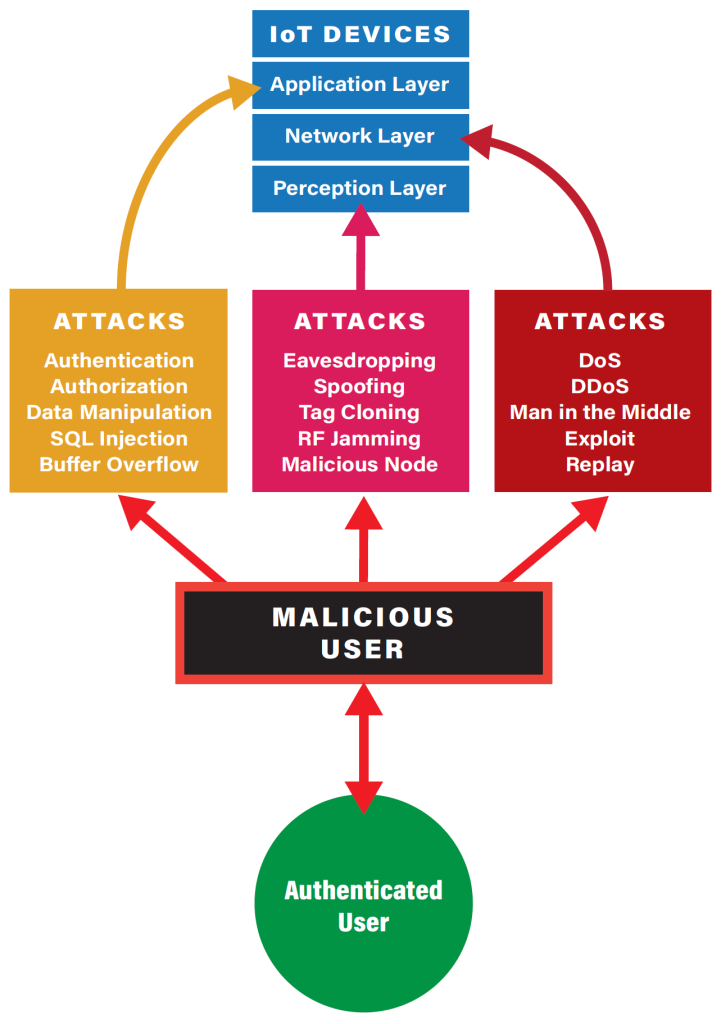
The graphic below shows how hackers can perform various malicious attacks on any system without security improvements or updates.[13]Chacko, A., & Hayajneh, T. (2018). “Security and privacy issues with IoT in healthcare.” EAI Endorsed Transactions on Pervasive Health and Technology, 4(14) … Continue reading Because the statistics show more than 50 percent probability of exploit success, it is a matter of time before half of the healthcare systems are hacked from outside threats, especially from Zero-Day attacks that, since new, are difficult to detect by intrusion and prevention systems (IDPS).[14]McGowan, A., Sittig, S., & Andel, T. (2021). “Medical Internet of Things: A Survey of the Current Threat and Vulnerability Landscape.” In Proceedings of the 54th Hawaii International … Continue reading Fortunately, based on the Palo Alto report, these account for only 3 percent of exploits.
Prevention
It is imperative to focus on security from a defensive perspective before an IoT system falls for ransomware. Security measures to prevent unauthorized access must use a high level of encryption, server backups, access controls, virus scanners, and up-to-date security software and updates. Data security is always a concern regardless of the type of industry in which the data is located.[15]Somasundaram, R., & Thirugnanam, M. (2021). “Review of security challenges in healthcare internet of things.” Wireless Networks, 27(8), 5503-5509.
Cybersecurity is a continuous process in which vendors and consumers must work unequivocally in sync. At this point, most healthcare centers appear to provide adequate security, but it’s impossible to verify since many if not most intrusions are never reported, due to the potential negative economic and reputational damage.
Encryption is critical, along with routine updates and constant research to understand the attack surface and help develop better-secured devices. A robust authentication algorithm will make it harder to access a device maliciously.[16]Kolokotronis, N., & Shiaeles, S. (Eds.). (2021). Cyber-Security Threats, Actors, and Dynamic Mitigation, CRC Press (2021). The Health Insurance Portability and Accountability Act (HIPAA) is responsible for the federal protection of individual healthcare data, while the National Institute of Standards and Technology (NIST) is the agency that promotes American innovation in technology to provide suitable security measures and guidelines to organizations, but more investment is needed to prevent data leaks and cyberattacks.
Many organizations choose not to upgrade their whole system by investing in new hardware and software, due to the massive cost and instead patch their systems. This enables breaches and even far more expensive ransomware attacks.[17]Loukaka, A., & Rahman, S. (2017). “Discovering new cyber protection approaches from a security professional prospective.” International Journal of Computer Networks & Communications … Continue reading
Since cyber-threat vectors are growing quickly, constant and rapid countermeasures need to be applied. Healthcare systems are increasingly being targeted because of the typical lack of security overall and because IoT devices are easily accessible. Cybercriminals understand not only how to exploit systems but also how to remain undetected for months after a breach.[18]Shepherd, A., Kesa, C., & Cooper, J. (2020). “Internet of Things (IOT) Medical Security: Taxonomy and Perception.” Issues in Information Systems, 21(3). Outsider attacks, however, are not as successful as insider attacks.[19]Chanal, P. M., & Kakkasageri, M. S. (2021). “Preserving Data Confidentiality in Internet of Things.” SN Computer Science, 2(1), 1-12. The configuration of internal systems is vital, therefore, and any error can become costly. Also, disgruntled employees might leave themselves backdoor access to extract or upload a virus to disrupt daily business needs. The security apparatus must be appropriately configured to target such specific threats. Individual health information is federally mandated to be protected, and medical facilities must understand the risk of using IoT devices without proper cybersecurity.[20]Nadikattu, R. R. (2020). “Data Safety and Integrity Issue in IoT.” International Journal for Research in Applied Science & Engineering Technology (IJRASET), 8(VI). [21]Mishra, B., & Padhy, N. (2021). “Enhancing the security, reliability, and data integrity issues in the internet of things by implementing blockchain strategy in mining: challenges and … Continue reading [22]Atlam, H. F., Azad, M. A., Alzahrani, A. G., & Wills, G. (2020). “A Review of Blockchain in Internet of Things and AI.” Big Data and Cognitive Computing, 4(4), 28.
Implementation
First, there is an important secure-oriented approach to make sure an IoT system is protected from cyber harm. The following approach is part of continuous computer hygiene that any organization or user can apply that involves changing default passwords, system patching, network segmentation, asset inventory and Bluetooth technology.
• Default Passwords
Computing hardware typically requires a password to authenticate. When a default password is provided, it needs to be changed by the user. Much stolen data is available on the Dark Web, a collection of internet sites accessible with a specialized browser, where users can buy and exchange stolen data. Good password hygiene must be alpha numeric with at least one special character and an uppercase. Also, the password must be changed every 60 to 90 days to prevent brute force attacks, which hackers use to discover passwords in plain text.
• Unpatched Systems
As with passwords, unpatched systems are a prime target for hackers and the main reason for the increased ransomware attacks. A patch management policy must automate security updates, as in Microsoft software, so that hardware and software are up to date, especially on critical systems.
• Network Segmentation
Network segmentation is imperative to limit malicious users from progressing from creating a breach to moving easily within the network and altering or stealing data. IoT devices must be located on a different system segment to be isolated from direct unauthorized access.
• Asset Inventory
Maintaining an active inventory of network-approved devices can facilitate patch implement when attacked, such that bad actors cannot use authorized or unauthorized devices to deploy malware and learn the system’s configuration or analyze data traffic.
• Bluetooth Connection
Bluetooth is the go-to method for IoT devices to connect to a network. However, Bluetooth is susceptible to a man-in-the-middle attack in which an attacker gets in between a user and the application—for example, by providing a free but malicious public WIFI hotspot—to eavesdrop or steal or alter the communication or data. Turning off the discoverable option when paired with a device is recommended so no malicious user can detect the connection since it’s invisible. Also, malicious hotspots typically aren’t password protected.
Second, integrity ensures that the data is not being altered by unauthorized users.[23]Tang, S., & Xie, Y. (2021). “Availability Modeling and Performance Improving of a Healthcare Internet of Things (IoT) System.” IoT, 2(2), 310-325. [24]Singh, R. P., Javaid, M., Haleem, A., & Suman, R. (2020). “Internet of things (IoT) applications to fight against COVID-19 pandemic.” Diabetes & Metabolic Syndrome: Clinical Research … Continue reading The mechanism also implemented for data confidentiality (protection against unauthorized access) can also benefit data integrity. Since the data cannot be viewed or deciphered, it cannot be altered in any way. It is equally essential to maintain such a system for access controls, data validation, audit trail, and, most importantly, data backup in case of total loss or inaccessibility as with a ransomware attack.
One proposed solution would be to enhance data security using a blockchain approach.[25]Stiawan, D., Suryani, M. E., Idris, M. Y., Aldalaien, M. N., Alsharif, N., & Budiarto, R. (2021). “Ping Flood Attack Pattern Recognition Using a K- Means algorithm in an Internet of Things … Continue reading Essentially, blockchain is information recorded in blocks that are highly difficult to breach, modify or access.[26]Shah, Y., & Sengupta, S. (2020, October). “A survey on Classification of Cyber-attacks on IoT and IIoT devices.” In 2020 11th IEEE Annual Ubiquitous Computing, Electronics & Mobile … Continue reading This technique is used with transactions of Bitcoins and other cryptocurrencies to protect transactions and their anonymity. Using blockchain with IoT devices would provide robust security and reduce organizational costs in rebuilding the database and exploited network post-attack.
Last, availability ensures that data can always be accessed flawlessly without interruption.[27]Fernandez, E. B. (2020). “A pattern for a Secure Cloud-Based IoT Architecture.” In Proceedings of the 27th Conference on Pattern Languages of Programs (PLOP”20). Association for Computing … Continue reading This is critical to using IoT devices in healthcare, since availability enables uninterrupted, real-time access to patient data for the proper diagnosis and monitoring. Ensuring availability requires investments in reliable data storage systems, secure Wi-Fi, an air-gapped network (which has no interface, wired or wireless, with outside networks) and the latest mobile technology operated properly. Also, critical areas of hospitals must be secured with a keypad access card, security officers and surveillance cameras.
The budget to implement a more efficient network system, especially if significant upgrading is required, might be expensive and time-consuming—but essential to security. Then once accomplished, the system’s implementation, maintenance and configuration must be constantly improved.
IoT devices are a growing technology that is becoming ubiquitous. Security concerns need to be addressed immediately to strengthen data integrity and availability.[28]Best, J. (2020). “Could implanted medical devices be hacked?” BMJ, 368. [29]Bhuyan, S. S., Kabir, U. Y., Escareno, J. M., Ector, K., Palakodeti, S., Wyant, D., & Dobalian, A. (2020). “Transforming healthcare cybersecurity from reactive to proactive: current status and … Continue reading
Banks, which protect people’s money, have far better security in place than the healthcare sector, which is required to protect people’s personal information, as well as their health and lives. It’s time for health to pay attention to wealth.
Alain Loukaka
Alain Loukaka, PhD, earned a BS in IT Networking, with an emphasis on cybersecurity, at Clayton State University, an MS in Information Technology at Florida Tech University and then a PhD in the Information Security and Information Assurance at Capella University. His exploratory research focused on cybersecurity exploits and advanced detection methods beyond current know applications. Loukaka has worked in the IT field for more than 15 years and plans to promote better security approaches and deterrents. For the last two years, he has served as an Application Support Consultant at the Oracle Corporation.
Shawon S. M. Rahman
Shawon S. M. Rahman, PhD, is a Professor of Computer Science and Engineering at the University of Hawaii at Hilo. He earned a BS in Chemical Engineering at Bangladesh University of Engineering & Technology, and an MS in Computer Science at NDSU and a PhD in Software Engineering also at NDSU. Prof. Rahman serves as the editor-in-chief of the International Journal on Cryptography and Information Security. He has also published more than 125 peer-reviewed articles. Prof. Rahman’s research interests include information assurance and security, digital forensics, software engineering education, software testing & QA, cloud computing, mobile application development and web accessibility. He belongs to many professional organizations, including IEEE, ACM, ASEE, ASQ, ISACA, ISCA and UPE.
References
| ↑1 | Palo Alto Networks, “2020 Unit 42 IoT Threat Report,” https://unit42.paloaltonetworks.com/iot-threat-report-2020/ |
|---|---|
| ↑2 | Joyia, G. J., Liaqat, R. M., Farooq, A., & Rehman, S. (2017). “Internet of medical things (IoMT): Applications, benefits and future challenges in healthcare domain.” J. Commun., 12(4), 240-247. July 7 |
| ↑3 | Zou, Y., Roundy, K., Tamersoy, A., Shintre, S., Roturier, J., & Schaub, F. (2020, April), “Examining the adoption and abandonment of security, privacy, and identity theft protection practices,” Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems, (pp. 1-15). |
| ↑4 | Humayun, M., Jhanjhi, N. Z., Alsayat, A., & Ponnusamy, V. (2021). “Internet of things and ransomware: Evolution, mitigation and prevention,” Egyptian Informatics Journal, 22(1), 105-117. |
| ↑5 | Leo, P., Isik, Ö., & Muhly, F. (2022). “The Ransomware Dilemma,” MIT Sloan Management Review, 63(4), 13-15. |
| ↑6 | Keary, J. (2022), “Rebuffing Russian Ransomware: How the United States Should Use the Colonial Pipeline and JBS USA Hackings as a Defense Guide for Ransomware,” Seton Hall University Law Library, 2022. |
| ↑7 | Mohurle, S., & Patil, M. (2017), “A brief study of wannacry threat: Ransomware attack 2017,” International Journal of Advanced Research in Computer Science, 8(5), 1938-1940. |
| ↑8 | Bunge, J., “JBS Paid $11 Million to Resolve Ransomware Attack,” Wall Street Journal, June 9, 2021. |
| ↑9 | Collier, K., “Major Russian-speaking ransomware gag behind JBS and Kaseya attacks goes offline,” NBC News, https://www.nbcnews.com/tech/tech-news/russian-speaking-ransomware-gang-goes-offline-rcna1403. |
| ↑10 | Yaqoob, I., Ahmed, E., ur Rehman, M. H., Ahmed, A. I. A., Al-garadi, M. A., Imran, M., & Guizani, M. (2017), “The rise of ransomware and emerging security challenges in the Internet of Things,” Computer Networks, 129, 444-458. |
| ↑11 | Hassija, V., Chamola, V., Bajpai, B. C., & Zeadally, S. (2021). “Security issues in implantable medic al devices: Fact or fiction?” Sustainable Cities and Society, 66, 102552 |
| ↑12 | Joyia, G. J., Liaqat, R. M., Farooq, A., & Rehman, S. (2017). “Internet of medical things (IoMT): Applications, benefits and future challenges in healthcare domain.” J. Commun., 12(4), 240-247. |
| ↑13 | Chacko, A., & Hayajneh, T. (2018). “Security and privacy issues with IoT in healthcare.” EAI Endorsed Transactions on Pervasive Health and Technology, 4(14) doi:http://dx.doi.org/10.4108/eai.13-7-2018.155079. |
| ↑14 | McGowan, A., Sittig, S., & Andel, T. (2021). “Medical Internet of Things: A Survey of the Current Threat and Vulnerability Landscape.” In Proceedings of the 54th Hawaii International Conference on System Sciences (p. 3850). |
| ↑15 | Somasundaram, R., & Thirugnanam, M. (2021). “Review of security challenges in healthcare internet of things.” Wireless Networks, 27(8), 5503-5509. |
| ↑16 | Kolokotronis, N., & Shiaeles, S. (Eds.). (2021). Cyber-Security Threats, Actors, and Dynamic Mitigation, CRC Press (2021). |
| ↑17 | Loukaka, A., & Rahman, S. (2017). “Discovering new cyber protection approaches from a security professional prospective.” International Journal of Computer Networks & Communications (IJCNC) Vol, 9. |
| ↑18 | Shepherd, A., Kesa, C., & Cooper, J. (2020). “Internet of Things (IOT) Medical Security: Taxonomy and Perception.” Issues in Information Systems, 21(3). |
| ↑19 | Chanal, P. M., & Kakkasageri, M. S. (2021). “Preserving Data Confidentiality in Internet of Things.” SN Computer Science, 2(1), 1-12. |
| ↑20 | Nadikattu, R. R. (2020). “Data Safety and Integrity Issue in IoT.” International Journal for Research in Applied Science & Engineering Technology (IJRASET), 8(VI). |
| ↑21 | Mishra, B., & Padhy, N. (2021). “Enhancing the security, reliability, and data integrity issues in the internet of things by implementing blockchain strategy in mining: challenges and solutions.” In Communication Software and Networks (pp. 137-144). Springer, Singapore. |
| ↑22 | Atlam, H. F., Azad, M. A., Alzahrani, A. G., & Wills, G. (2020). “A Review of Blockchain in Internet of Things and AI.” Big Data and Cognitive Computing, 4(4), 28. |
| ↑23 | Tang, S., & Xie, Y. (2021). “Availability Modeling and Performance Improving of a Healthcare Internet of Things (IoT) System.” IoT, 2(2), 310-325. |
| ↑24 | Singh, R. P., Javaid, M., Haleem, A., & Suman, R. (2020). “Internet of things (IoT) applications to fight against COVID-19 pandemic.” Diabetes & Metabolic Syndrome: Clinical Research & Reviews, 14(4), 521-524. |
| ↑25 | Stiawan, D., Suryani, M. E., Idris, M. Y., Aldalaien, M. N., Alsharif, N., & Budiarto, R. (2021). “Ping Flood Attack Pattern Recognition Using a K- Means algorithm in an Internet of Things (IoT) Network.” IEEE Access, 9, 116475-116484. |
| ↑26 | Shah, Y., & Sengupta, S. (2020, October). “A survey on Classification of Cyber-attacks on IoT and IIoT devices.” In 2020 11th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON) (pp. 0406-0413). IEEE. |
| ↑27 | Fernandez, E. B. (2020). “A pattern for a Secure Cloud-Based IoT Architecture.” In Proceedings of the 27th Conference on Pattern Languages of Programs (PLOP”20). Association for Computing Machinery, USA. |
| ↑28 | Best, J. (2020). “Could implanted medical devices be hacked?” BMJ, 368. |
| ↑29 | Bhuyan, S. S., Kabir, U. Y., Escareno, J. M., Ector, K., Palakodeti, S., Wyant, D., & Dobalian, A. (2020). “Transforming healthcare cybersecurity from reactive to proactive: current status and future recommendations.” Journal of Medical Systems, 44(5), 1-9. |

