
Above, a 1976 photo of Viki Wegerle, who was strangled with a nylon stocking by the BTK killer in her home on September 16, 1986. She was married and the mother of a two-year-old.
ON JANUARY 15, 1974, four members of the Otero family were murdered in their home in Wichita, Kansas. Joseph and Julie Otero and their two youngest children, Joseph Jr. (Joey) and Josephine (Josie), ages 9 and 11, were found dead by their oldest son Charlie and siblings Carmen and Danny, when they returned home from school. All four victims had been bound and strangled, and the phone line to their house had been cut.
A few months later, on April 4, Kathryn Bright was stabbed to death in her Wichita home, while her brother was shot twice in the head but fortunately survived. The phone line to the Bright’s home had also been cut.
In October 1974, after a confession to the Otero murders was publicized—and later proven false— Wichita police received a phone call directing them to a mechanical engineering textbook on the second floor of the Wichita Public Library across the street from police headquarters. Inside the book was a letter written by someone claiming to be the real killer. The letter contained previously unpublicized details of the Otero deaths, along with the killer identifying himself with the code initials B.T.K., which the self-alleging killer wrote stood for “Bind them, Torture them, Kill them.”
In 1977, there were two more strangulation victims, Shirley Vian and Nancy Fox. Early the following year, another taunt, this time in the form of a poem, was sent to The Wichita Eagle, the city’s largest daily newspaper and, a few weeks later, another message arrived at KAKE-TV in Wichita. These prompted the Wichita police to reveal for the first time the presence of “The BTK Strangler,” alerting residents that a serial killer was operating in the area.
No more murders were attributed to BTK for more than seven years until the strangulation of Marnie Hedge on April 27, 1985, and then Vicki Wegerle on September 16, 1986. BTK’s final known victim was Dolores Davis, who was strangled and dumped near a bridge on January 19, 1991.

With the help of the FBI, Wichita police hunted for BTK, while being taunted with a series of clues left by the killer. Messages in public locations and sent to news media, along with packages with disturbing drawings depicting the murders and dolls posed in the positions of the victims.
After the 1991 murder, BTK seemed to disappear, until a story in The Wichita Eagle in 2004 implied that BTK was a distant memory. Then letters and packages from BTK began arriving again at local newspapers and television stations and even left in a garbage bag in Murdoch Park in Wichita. The letters and packages contained mementos from the victims, as well as drawings and puzzles with clues to the killer’s identity.
In late January 2005, an employee at a local store found a cereal box in the back of his truck with a note asking whether BTK could communicate with police via a computer floppy disk without being traced. The police were instructed to run a newspaper ad with the message: “Rex, it will be OK,” if this was true.i
After the police ran the ad, a package arrived at KSAS-TV in Wichita with a clue that ultimately would lead to catching the BTK killer.i That clue was uncovered with digital forensics, which did not exist during much of BTK’s killing spree.
Evolution of Digital Forensics
Digital evidence is associated with approximately 90 percent of crimes committed today. Although the first known computer crimes were in the 1970s, the origins of the relatively new field of digital forensics can be traced to the mid-1980s and early 1990s. BTK killed his last victim in 1991 at the dawn of the digital forensics era. In the early days, with the growing popularity of personal computers, it was known as “computer forensics” and recognized early on by law enforcement as a source of evidence in crimes. Prior to the digital age, data was stored differently. Boxes and filing cabinets of paper and letters became bytes and files on floppy disks, hard drives and servers. The country’s first official digital forensics program was the FBI’s Magnet Media Program launched in 1984.ii This evolved into FBI’s Computer Analysis Response Team (CART).
Evidence found on personal computers evolved into evidence being located on multiple computers of small local networks. The growing popularity of the internet led to looking for evidence in data sent and retrieved over the internet. That, along with the later invention of cellphones and Internet of Things (IoT) devices, caused investigators to look beyond computers to other devices, including video gaming consoles, smart TVs, smart watches and vehicles.
Computer forensics became digital forensics to encompass all the different ways data could be stored or transmitted. Early tools consisted of data recovery software and command line tools (commands that a user types in directly for execution), with the first commercial software being developed in the 1990s and marketed to law enforcement. Forensics teams usually consisted of members of law enforcement officers who were computer hobbyists or had some type of computer background. Those officers tasked with investigating crimes had limited training and no official framework to follow to ensure repeatability in their investigations.
What Is Digital Forensics?
Digital forensics is the identification, preservation, analysis, reporting and presentation of data stored digitally. To reach the last step of presentation, in a criminal case in a court of law, the previous steps should be followed and done in a manner that can be repeated. By starting with proper identification, preserving the data contained on the collected device, analyzing that extracted data, and documenting every person, tool and action that has been carried out, the chain of custody is established. Following these steps provides assurances that the results of an investigation are acceptable for presentation in court.
Identification
Digital evidence has evolved from floppy disks and hard drives to include a myriad of devices, such as cellphones, drones, GPS, vehicles, internet data, cloud data and other devices that store or transmit data. Identifying devices at a crime scene can be critical to an investigation when a memory card can be as small as a fingernail, or a USB drive can be disguised as a tube of lipstick. Hard drives have been found glued to the underside of tables or hidden in ceiling tiles. By the early 2000s, the everyday use of floppy disks was on the decline when, in February 2005, a package arrived at KSAS-TV in Wichita from BTK containing a floppy disk. That disk would hold the missing clue to BTK’s identity.
Preservation
Digital evidence can be very volatile in nature, and steps must be taken to ensure that it isn’t tampered with. Collecting digital evidence properly can be the difference between having valuable evidentiary data or having no data. Cellphones can be accessed remotely by a suspect to wipe data if they are not collected and stored properly. An unknown password on a phone or encrypted computer can be the difference between accessing the data or having it locked permanently away out of reach of investigators. Every effort is made to create a digital copy of the data prior to analysis. Working from a copy of the data maintains the integrity of the data on the original device, avoiding any question of tampering or altering the evidence. On the occasion that a digital copy cannot be obtained, and the data must be viewed on the device itself, every step must be documented to ensure that the proper steps are followed.
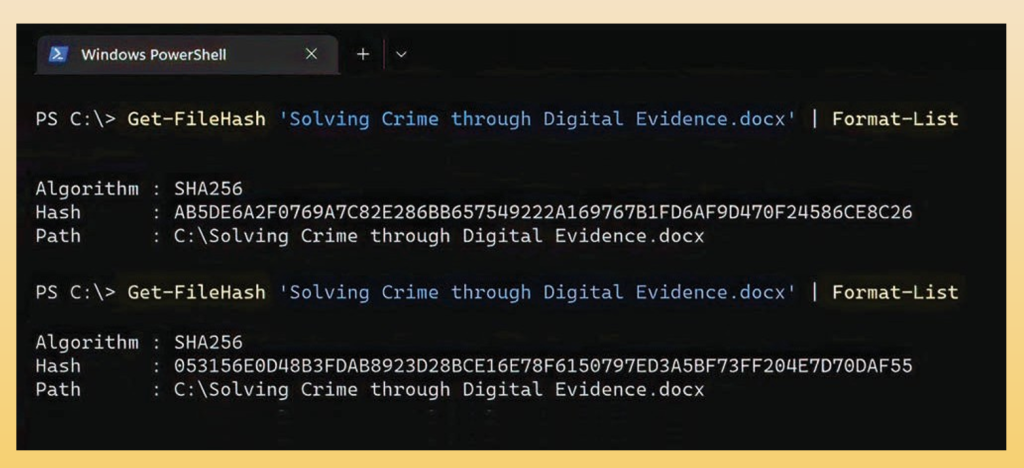
The integrity of data recovered from devices is ensured using hashing. A hash function is a one-way cryptographic algorithm that, when applied to data, produces a unique output. Changing even one byte in the input data results in a different hash value. If thinking of this in terms of a picture, changing one pixel will result in a different hash value than the original. Another example is even adding an extra space in a document, which can’t be easily seen, alters the hash value, as shown in the illustration below, using the SHA256 algorithm.
Analysis
During analysis, the analyst is looking for data that can serve as evidence that supports or refutes the case being investigated. Modern digital forensics tools, which comb through the vast amounts of data that can come during an investigation, make analysis easier than in the past. Each device that is examined and the level of access that can be obtained to the device’s data can vary based on the version of the operating system installed, the hardware contained within the device and other factors. The data on a device can include information such as emails, images, internet search history, documents, videos, chat information, and the device might also include deleted or hidden data. On a floppy disk, hard drive, USB stick or other similar storage device, deleted files remain available until overwritten by other data.
When analyzing that data, the investigator is trying to determine who created the data, what type of device created the data, when the data was created or modified, where the data was created and answers to other pertinent questions. In the BTK case, the floppy disk the killer sent had been used to send a document to the television station; however, it had previously contained other documents that the killer had deleted. The documents were still available, not having yet been overwritten by other data, and they were able to be recovered by investigators and analyzed.
Reporting
Reporting is an important step in the digital forensics process. Analysts know what they see, but being able to interpret and describe that data in a report, which can be understood by non-experts, is a skill that is developed over time. Reporting must detail the steps the analyst took during the investigation, as well as tell the story of the significance of what was found, or not found, during the analysis of the data. Since reporting aids in the next step of presentation, which may be to a jury trial, reports need to be written for any audience regardless of their technical background.
Reporting should tell the story that the device has taken since arrival, detailing the acquisition of the evidence, everything done with the device while it was being examined, what evidentiary findings were located in the data recovered from the device and finally the return of the evidence in order to document the proper chain of custody. Detailed reports that include the proper handling of the evidence being reported on can avoid later accusations of improper handling or tampering of evidence.
Presentation
Presenting digital evidence to a jury during a trial can be challenging when compared to presenting physical evidence such as paper documents or photographs. Explaining how data is stored on a device requires someone who can speak to the jury in a way they can understand. It isn’t always as simple as handing jury members a document they can read or a photograph that they can see. Lawyers need to understand digital evidence and what is important to their case. The expert witnesses called to testify must be able to talk to the jury about their findings in a way that reflects the importance of the evidence without getting overly technical.
Challenges
There are many challenges in digital forensics, from the continuous development of software and hardware to new encryption techniques. It is a cat-and-mouse game between law enforcement agencies and technology companies to stay one step ahead. Privacy advocates are on the side of end-to-end encryption to keep data private, however that privacy can also hide criminal behavior.
Volume
The sheer volume of devices and data is a challenge for investigators both in storage and analysis. According to Deloitte (a leading global provider of audit, consulting, advisory and tax services), the average household has 22 connected devices including laptops, phones, smart watches, smart home devices, which can store data—sometimes, a lot of data.iii
Modern smart phones can have up to 1 terabyte (TB) of storage. To put that in perspective, it would take 728,177 floppy disks to store 1TB of information.iv Finding a document like the one left by BTK becomes much more difficult when looking through 728,177 items than just 1 item. The number of devices and the vast amounts of data to be analyzed lead to backlogs in casework, as well as stress and burnout for investigators and analysts.
Encryption
Encryption poses a challenge with modern devices containing whole device encryption.v Encryption uses a mathematical algorithm to scramble readable text so that only someone with the correct decryption code can understand it. Previously, a hard drive could be removed from a computer or chip removed from a phone, albeit not always easily, and the data read and analyzed. Modern devices that employ encryption techniques on the hardware level rather than file-based encryption present additional challenges. The hard drives or chips can still be removed and read, however the data that is recovered is encrypted, so while the data is still able to be retrieved, it cannot be interpreted due to the encryption. The only way to access the data held within that encrypted device is with the user’s passcode. If the passcode is unable to be recovered, from the user or through technological means, that data remains inaccessible.
Emerging Devices & Platforms
Along with encryption, new technology in both new devices and upgrades to existing technology, such as a newer operating system on a computer or cellphone, presents challenges. Devices such as drones, vehicles, Apple AirTags or home security cameras are introduced constantly. Technology companies are continuously upgrading their operating systems and the techniques to keep their devices secure from cyberattacks and other vulnerabilities. Combine that with the multitude of applications available on multiple platforms, and it takes a tremendous effort by the companies creating digital forensics tools to both access the devices and process data from installed applications. The introduction of a new chat application on a smartphone requires software engineers who can then decode that data to understand how it is stored and make it easily readable for forensic analysts or analysts digging deep into the database to find the data and manually linking tables stored within the database to find the stored communications—a time-consuming process.
Burnout & Staff Turnover
Digital forensics analysts are at high risk for burnout. The workload demands, due to the vast amounts of incoming devices and data, along with the material such as documents, images or videos that analysts are often exposed to that can contain violence or child exploitation content, can lead to workplace stress, reduced efficacy, absenteeism, early retirement and burnout.

Nature of Digital Evidence
Digital evidence requires different tools and techniques than physical evidence for identification, collection and analysis. Instead of blood or fingerprint evidence, digital evidence consists of information and data. Both physical and digital evidence can be volatile in that they might not be present for a long time. Blood can wash away, fingerprints can smudge, and digital evidence can disappear. For example, computer memory can vanish if the computer is powered down. However, digital evidence is wider in scope, can be mobile and is much more personal in nature. The National Institute of Justice defines digital evidence as: “Information and data of value to an investigation that is stored on, retrieved or transmitted by an electronic device.”vi
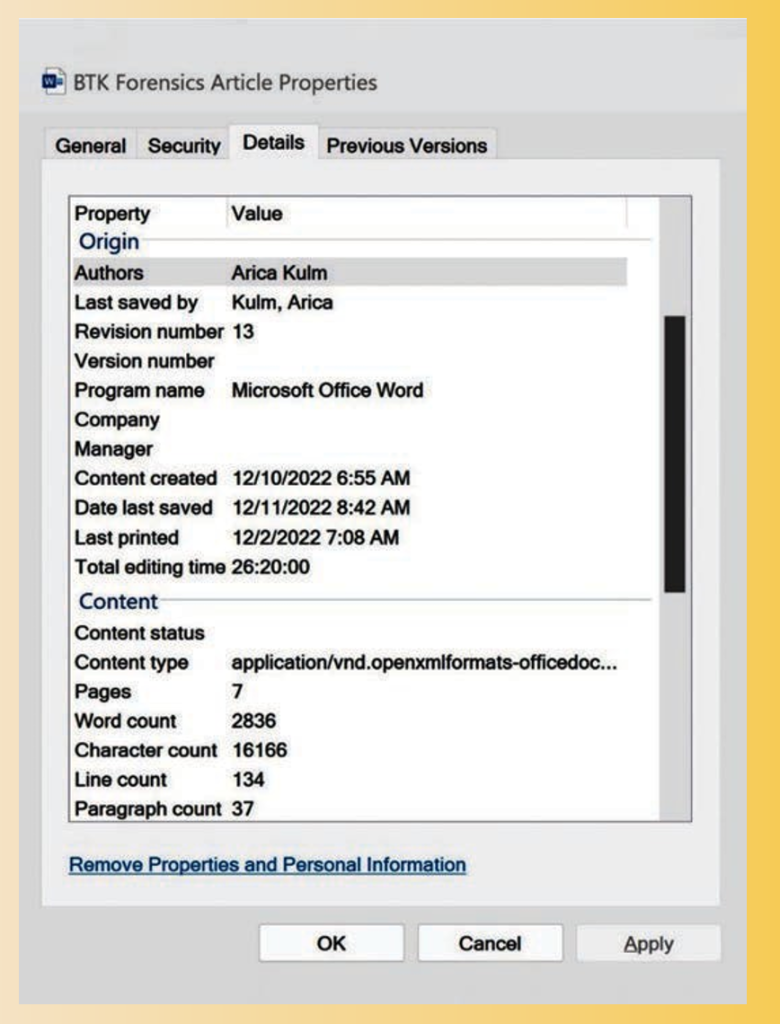
Computers and cellphones can hold the most personal material from banking information to conversations to pictures and videos. Pouring through that information is often akin to reading someone’s diary or inner-most thoughts. Chat conversations with friends and loved ones, internet searches conducted, locations visited, pictures and videos captured and shared. The metadata found within a document or image can be enough to place someone at a location or identify him or her as a person of interest and make the difference in an investigation, as in the BTK case.
Metadata is defined as “data about data.” Metadata describes data and can provide information about the item of interest (for example, a document, image or video), such as who created it, what type of device created it, when it was created, where it was created. In the BTK case, deleted documents found on the floppy disk sent to the television station contained metadata, which indicated that the disk had been used at Christ Lutheran Church in Wichita by a user named “Dennis.” That was the clue police needed that soon led them to the church’s council president. After 30 years of searching for the BTK killer, on February 25, 2005, within 10 days of that floppy disk arriving at the television station, BTK was identified, arrested and confessed to the killing of 10 people.
Future
The volume of both devices and data will drive the digital forensics field toward automation. Artificial intelligence (AI) and machine learning (ML) will assist with analyzing and categorizing data faster. Unlike live analysts, AI applications don’t show fatigue and are not affected by graphic material. Using automation to complete some of the time-consuming activities can free up analysts to fine tune and do the detail work. AI and deep-learning algorithms can be used to review things, such as documents, looking for relevant information.
Digital forensics tools have begun to move toward collaborative cloud-based environments allowing more than one analyst to work on the same investigation simultaneously. This can aid in environments where investigators are working on the same case from different locations. These types of tools can also provide analytics to look for trends across different cases. Link analysis can show relationships between data recovered from multiple devices.
Wrap-Up
Digital forensics is a broad field with many specialties. So far this article has addressed digital forensics from the perspective of a law enforcement investigation, however there are many additional aspects of digital forensics. Increasingly, data is being stored in the cloud rather than on servers and workstations. Data travels across networks to get to that cloud storage with the potential for data breaches. Investigating how or where data breaches occur is a branch of digital forensics as well as cloud forensics. In addition to law enforcement, corporations need digital forensic analysts to investigate data breaches, intrusions, insider threats, theft of corporate property and violations of acceptable use policy. The increasingly connected world brings more and more opportunities for digital forensics to play an important role in helping to solve crimes.
References
i R.J. Rosen, “The Floppy Did Me In,” The Atlantic, 16 January 2014. [Online]. Available: https://www.theatlantic.com/technology/archive/2014/01/the-floppy-did- me-in/283132/. [Accessed 27 November 2022].
ii S. Moore, “What is Digital Forensics?,” [Online]. Available: https://www. azolifesciences.com/article/What-is-Digital-Forensics.aspx.
iii J. Arbanas, J. Loucks and S. Hupfer, “Connectivity and Mobile Trends Survey: Mastering the New Digital Life,” The Wall Street Journal, 20 September 2022. [Online]. Available: https://deloitte.wsj.com/articles/connectivity-and-mobile-trends- survey-mastering-the-new-digital-life-01663699532. [Accessed 27 November 2022].
iv T. Fisher, “Terabytes, Gigabytes, & Petabytes: How Big Are They?,” 1 January 2021. [Online]. Available: https://www.lifewire.com/terabytes-gigabytes-amp- petabytes-how-big-are-they-4125169. [Accessed 27 November 2022].
v For a primer in encryption, please refer to: Marcus Fries, PhD, “The Unencrypted History of Cryptography,” Dakota Digital Review, North Dakota University System, Fall-Winter 2023, https://dda.ndus.edu/ddreview/the- unencrypted-history-of-cryptography/
vi M. B. Mukasey, J. L. Sedgwick and D. W. Hagy, “Electronic Crime Scene Investigation: A Guide for First Responders, Second Edition,” U.S. Department of Justice, Washington, DC, 2008.
ARICA KULM, PHD Director of Digital Forensics Services Dakota State University
Arica Kulm, PhD, is the Director of Digital Forensic Services at the DigForCE Lab at Dakota State University. Her team works with clients to execute a variety of digital forensic supports for investigations with law enforcement agencies and cybercrime investigations for South Dakota Consumer Protection and other organizations. She also leads teams that provide free cybersecurity assessments for South Dakota cities and counties through the Project Boundary Fence. Kulm earned a bachelor’s degree from South Dakota State University, and her master’s and doctorate degrees in Cyber Defense from Dakota State University. She also holds several industry certifications. Her doctoral dissertation resulted in a patent on a digital forensic tool. Kulm’s research interests include the dark web and dark web host-based forensics. She is a much sought-after presenter at various conferences and trainings, and as a spokesperson for media engagements.

