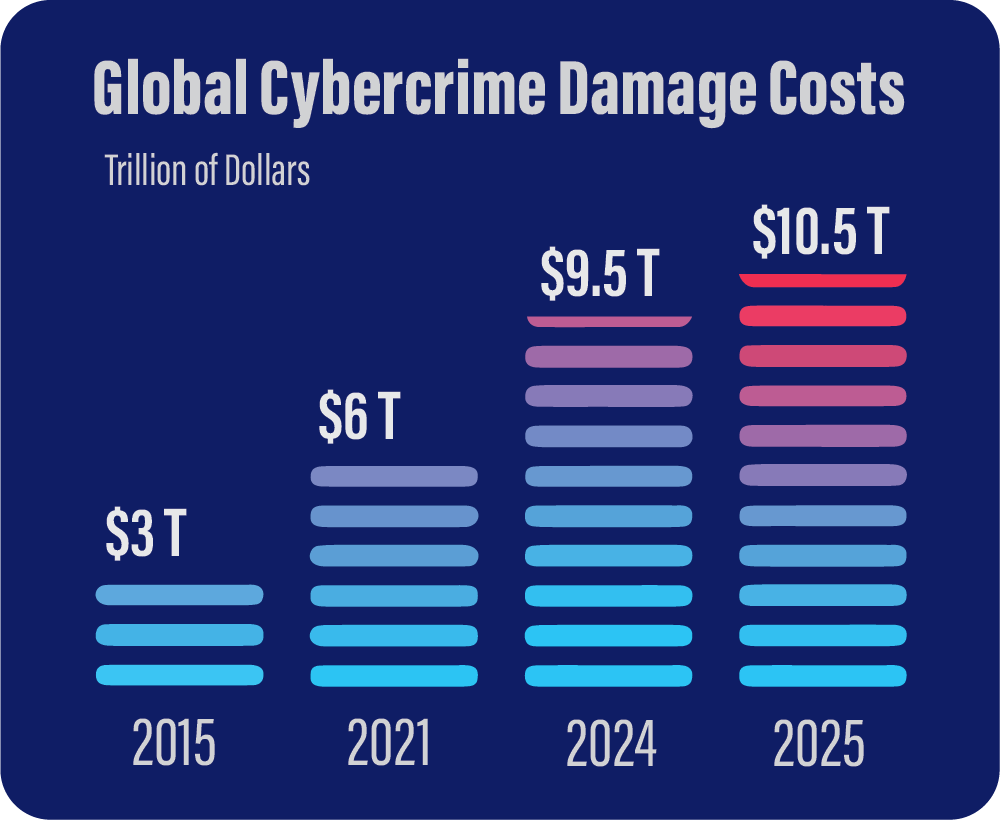
The cost of cybercrime is escalating globally. By 2025, it’s projected to reach $10.5 trillion annually.i This figure is more than just a number; it demonstrates the increasing sophistication of cyberthreats and the escalating stakes for businesses and governments worldwide. Geographically, the cost of cybercrime varies. The U.S, for example, has been hit hard, with cybercrime victims losing an estimated $42.9 billion in 2023.ii
These figures highlight the urgency for businesses and governments to invest in robust cybersecurity measures and policies. Implementing a robust security strategy is critical to prevent cyberthreats. In recent years, the cybersecurity landscape has undergone significant transformations, evidenced by the foregoing, as well as numerous other indicators. The e-commerce environment is now less predictable than it once was and complicated, due to geopolitical and economic factors. It is under constant cyberthreats.
The advancement of digital technologies has precipitated a new era of cybersecurity threats, as cybercriminals are now implementing more sophisticated methods that enable them to exploit vulnerabilities and gain unauthorized access to sensitive data and information. Cybercriminals are also exploiting AI by using AI-powered malware, phishing scams and social engineering attacks.iii These are growing rapidly worldwide and pose a significant risk to businesses, organizations and individuals.
Not all threats are external, though. The “Trellix 2024 Threat Predictions” report concluded that insider threats are emerging as growing security concerns. Insider threats come from someone who works for or has access to an organization’s data and systems. An insider threat could be an employee, a contractor, a partner or a former member of an organization. The report, based on recent business and industry analysis, showed that “insider threats have increased by 47 percent over the last two years, incurring a total loss of $15.38 million.”iv
Another big challenge is advanced persistent threats (APTs). These are threats by which an attacker, often a nation-state or nation-state-sponsored group, gains unauthorized access to a network and retains undetected system access for an extended period. These attackers are typically well-resourced and execute sophisticated malicious cyber activity targeted at prolonged network or system intrusion.
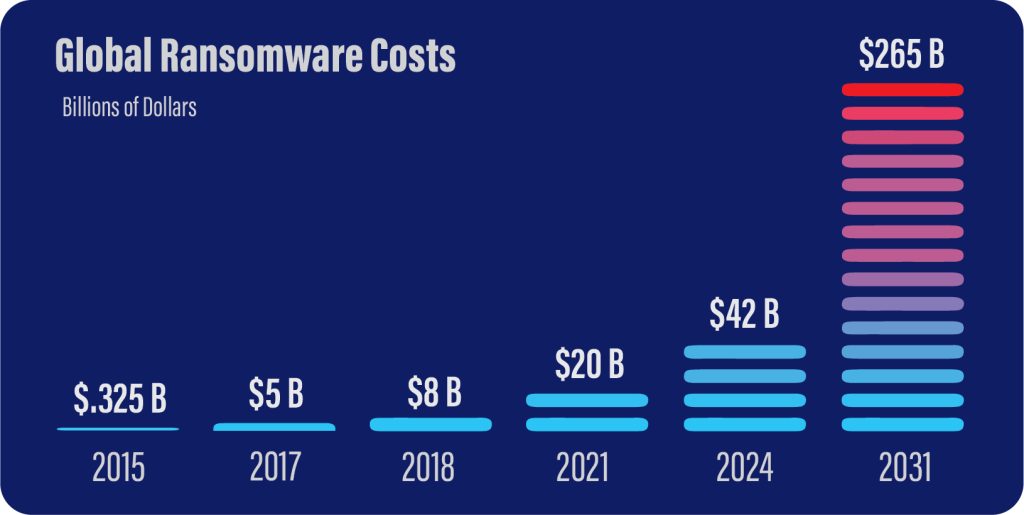
Cybersecurity Ventures has predicted that ransomware will remain a major threat to businesses. Ransomware attacks pose severe risks to operations and finances by encrypting files and systems, and demanding ransom payments to unlock them.v In some cases, files are not returned or are publicly released—even after a ransom is paid. Other significant threats include business email compromise scams, which produced 1,153 cyber-insurance claims in 2022.vi
A cyber incident can create a nightmare for a business. It has a negative financial impact. However, the impact can go beyond money and put the company’s reputation at risk, resulting in the loss of customers and investors.
Cyber Insurance: Purpose & Essence
In today’s digital world, unseen cyberthreats can overcome even the most robust defenses. Cyber insurance can serve as a form of ‘virtual shield’ and provide a safety net to minimize financial damage following an incident. Cyber insurance can cover a wide range of expenses—including regulatory fines, legal fees, forensic investigations and data recovery—and costs associated with business interruptions. In the event of a breach, it can cover all or part of the substantial cost of notifying affected customers and may provide access to professional response teams, enabling swift and effective incident management. Cyber insurance also typically covers some or all costs associated with damages and recovery following attacks such as ransomware and data breaches. It can also provide financial protection against lawsuits, extortion payments and compliance fines. Notably, the coverage provided by cyber insurance has been changing, in recent years, due to losses faced by insurers and other market factors, so it is critical for a business to understand the coverage provided by its particular policy.
Cyber insurance can encourage effective cybersecurity procedures and may provide experts to help with each stage of the recovery procedure. The digital world is a never-ending game of evolution, adaptation and risk, in which cyber insurance can help competency and resilience.
Based on recent projections, the cyber-insurance market is anticipated to grow to $20.6 billion by 2025.vii Much of this growth is likely in response to the surge in cyberattacks over the past few years. Cyberattacks increased by 50 percent from 2020 to 2021, far more than businesses or insurers had anticipated.
Left, Not only is cybercrime growing by 15 percent per year, “[o]rganized cybercrime entities are joining forces, and their likelihood of detection and prosecution is estimated to be as low as 0.05 percent in the U.S., according to the World Economic Forum’s 2020 Global Risk Report.”
According to the World Economic Forum’s “The Global Cybersecurity Outlook 2023,” cyber and business leaders said identity theft, followed by cyber extortion—including ransomware—concerned them most in regard to their personal cybersecurity.
Tailored Cyber-Insurance Policies
When shopping for cyber insurance, it’s crucial to first identify an organization’s vulnerabilities. Whether it’s a large healthcare organization, responsible for safeguarding critical medical records, or a small, rapidly growing company protecting client secrets. Each scenario presents its own set of challenges.
Cyber-insurance coverage should be specifically tailored to address each provider’s unique risks, including those prevalent in different industries.
For instance, a manufacturer might desire a policy addressing threats, such as industrial espionage and disruption of production lines. A firm in the finance sector, which handles sensitive data, might seek coverage for such threats as data breaches and financial fraud. Similarly, a healthcare provider, which has sensitive medical records, might seek coverage for threats such as patient data breaches and ransomware attacks. An education sector organization, which holds vast amounts of personal and research data, might want coverage for threats including unauthorized access and data theft.
The next question is, what are a company’s most valuable cyber assets? Intellectual property or financial transactions, for example? The cyber-insurance policy might need to explicitly cover threats against such high-value assets.
Virtual walls alone do not make a fortress. Generic cyber insurance is unlikely to provide the needed coverage for neither a sprawling healthcare giant nor an agile startup. These firms might want precise customized coverage. Startups, for example, might concentrate on social media hacking and web threats, while a healthcare giant might seek protection against breaches involving patient-sensitive data, especially since they must comply with healthcare standards along with protecting IT infrastructure. Problematically, neither firm might be able to get exactly what they desire, as the startup might be too small to procure (or afford) a custom policy, and the risks posed by the large healthcare firm might be beyond what cyber insurers are willing to cover.
A robust cyber-insurance policy is not just a financial safety net, it’s also an investment in a firm’s future. By reducing the exposure to potential liabilities and helping restore operations, cyber insurance can prevent a cyber event from leading to business closure.
Minimize Risk & Exposure
Utilizing security measures to lessen the impact of cybersecurity threats is known as cybersecurity risk mitigation. Proactive steps include employee training, implementing security controls and employing defensive technologies such as firewalls. Many providers require a minimum level of cyber maturity to write a policy, and some reward good security practices with discounts. These measures also make a business less desirable as a target for hackers.
There are three essential components involved:
Prevention: The goal of prevention is to avert problems through techniques such as strong passwords, firewalls and employee training.
Detection: Threats are promptly identified through monitoring systems in the detection process.
Response & Remediation: Taking prompt action to mitigate and recover from attack losses.
It is imperative to consistently update, test and modify these strategies due to the constantly evolving cyberthreat landscape. Proactive cybersecurity risk mitigation is crucial, as virtually all organizations have some exposure to cyberattack threats.
Here are some strategies for mitigating cybersecurity incidents across the IT ecosystem:
- Evaluate cybersecurity risks, find vulnerabilities and rank fixes in order of importance. Several firms provide evaluations based on data from public and private sources. Security ratings can help organizations monitor, benchmark and improve their security posture, as well as communicate their security performance to external stakeholders. By combining ratings with a risk assessment, cyber risks can be identified and addressed in a dynamic and data-driven manner, strengthening defenses against attacks and providing ongoing insights into security performance.
- Establish network-access controls after conducting an asset assessment to minimize insider and external threats. To ensure that only the right people can access the right data, what kind of job each person has, and what kind of data is needed must be verified. A zero-trust system can be used to help prevent mistakes or misuse by employees and provide a barrier against both internal and external threats.
- Installing firewalls and antivirus software will improve cybersecurity. While antivirus software looks for possible threats, firewalls serve as a barrier, regulating incoming and outgoing traffic. These tools must be configured correctly and updated often to be effective. Make sure that the selected antivirus software can detect new malware and customize firewalls to meet the company’s needs.
Regular audits and updates also strengthen overall security, reducing vulnerability to cyberattacks. Proactive action is necessary to lower cybersecurity risks, particularly in light of the numerous cyberattacks worldwide every day, through which thousands of people fall victim to hackers every year.viii
Network traffic should be continuously monitored to provide real-time threat detection and insights into IT ecosystems. This monitoring entails utilizing cutting-edge equipment and knowledgeable staff for in-depth analysis, guaranteeing prompt reactions to anomalous activity and lessening the likelihood of successful attacks. Using continuous monitoring helps organizations stay ahead of threats in the constantly shifting digital landscape by supporting compliance with cybersecurity standards.
- Finally, employees need cybersecurity training, emphasizing five important points:
- Employees should be educated about cybercrime strategies and trained in identifying phishing emails, links and attachments.
- Employees should be taught how to make strong passwords, along with the value of frequent updates. To increase security, firms should use multifactor authentication, and password reuse should be avoided.
- Employees should learn how to identify sensitive data and how to handle it appropriately. They should only share data with people who need it and have the right to access it. This is called the principle of least privilege, which reduces the risk of unauthorized access or misuse of data. Role-based access control assigns roles to users, based on their job functions and responsibilities, and allows system administrators to grant or deny permissions to users based on their roles. Employees who are tasked with transmitting or storing data should be trained in the proper ways to do so.
- Organization IT staff members should ensure that they keep software, drivers and device firmware up to date.
- Employees should be taught to avoid dangerous websites and how to secure mobile devices when using remote access to company resources.
Organizations should require staff members to be vigilant when sharing sensitive information and to recognize social-engineering tactics. They should create a pathway to and require reporting of suspicious incidents and foster a cybersecurity-aware culture.
By implementing these proactive defense strategies, organizations reduce their likelihood of becoming victims of a successful cyberattack and might also enjoy cyber-insurance discounts.
Choosing the Right Armor
The cyber-insurance market is growing rapidly. “According to data shared by global ratings agencies Fitch and Standard & Poor’s (S&P), the U.S. market is 80 percent concentrated in the hands of 15 insurance companies.”ix Choosing a cyber-insurance provider among these or other firms with less market share is not a simple task. There are many factors to consider, such as coverage, limits, deductibles, exclusions, premiums, and a provider’s response and claims process. There is also a need to evaluate the reputation, financial strength and customer service of the provider.
It is important to recognize that each insurer’s policies and coverage options may differ and to select a policy that best matches a company’s needs. Insurers also evaluate organizations’ cyber-risk exposure to determine the level of protection they are willing to provide and the limitations they will apply to that protection.
Organizations should consider factors such as the type, volume and sensitivity of the data handled; the industry regulations and standards that require compliance; the potential impact of a cyber incident on operations, revenue and reputation; and the existing security measures and controls in place. They may also wish to invest in cybersecurity measures such as defensive technologies or specialized service providers. Before deciding on insurance needs, organizations can benefit from conducting comprehensive assessments, such as a security audit, to understand their current cybersecurity posture.
Organizations might also wish to consult with a cyber-risk advisor or broker who can help them understand the cyber-insurance market, analyze their cyber-risk profile, recommend cyber-insurance options for the company, negotiate the terms and conditions with insurers, and assist with the claims process, if needed. An advisor can help with purchasing cyber insurance, especially if the business is not familiar with insurance language and terms. An advisor can also aid an organization in understanding the risks it faces and recommend the coverage options based on identified needs.
Organizations should pay attention to the details of the policy, such as what is covered and what is not, how coverage is triggered, how limits and sub-limits are applied, how deductibles and coinsurance are calculated, and how premiums and discounts are determined. Finally, organizations should review the insurer’s claims process and support services. Find out how easy and fast it is to report a claim; how the provider handles the investigation and settlement of the claim, and what kind of assistance and resources the provider offers in response to a cyberattack. These can include services, such as incident response teams, forensic experts, legal counsel, public relations specialists and cyber-risk management tools.
Given its role in covering costs associated with cyberattacks, cyber insurance can be an important component of organizations’ cyber-risk management strategy. However, cyber insurance is not a replacement for cybersecurity, as it cannot prevent or stop a cyberattack from occurring. A robust cybersecurity strategy is also required.
This article has been updated from the printed version. ◉
References
i https://cybersecurityventures.com/cybercrime-damage-costs-10-trillion- by-2025/ ii https://www.comparitech.com/blog/vpn-privacy/cybercrime-cost/ iii https://www.darkreading.com/vulnerabilities-threats/growing-cyber-threats-of- generative-ai-who-is-accountable iv https://www.trellix.com/about/newsroom/stories/research/trellix-2024-threat- predictions/ v https://cybersecurityventures.com/cybersecurity-boardroom-report-2023/ vi https://www.getastra.com/blog/security-audit/cyber-insurance-claims- statistics/ vii https://www.globaldata.com/media/insurance/cyber-insurance-industry- exceed-20bn-2025-says-globaldata/ viii https://us.norton.com/blog/emerging-threats/cybersecurity-statistics ix https://www.nsinsurance.com/analysis/biggest-us-cyber-insurance-companies/
Zia Muhammad
Zia Muhammad is a cybersecurity researcher and a PhD candidate at NDSU’s Department of Computer Science, and a Mancur Olson Graduate Fellow at NDSU’s Challey Institute. Previously, he was a lecturer at the Department of Cybersecurity, Air University. Muhammad also worked as a researcher at the National Cyber Security Auditing and Evaluation Lab (NCSAEL). Muhammad has authored several peer-reviewed publications presented at conferences and published in cybersecurity journals. He earned a BS in Software Engineering at the University of Engineering and Technology (UET-Taxila) and an MS in Information Security at the National University of Sciences and Technology (NUST), both in Pakistan. He expects to earn his PhD in Software and Security Engineering at NDSU in the fall of 2024.
Jeremy Straub, PhD, is an Assistant Professor in the North Dakota State University Department of Computer Science and a NDSU Challey Institute Faculty Fellow. His research spans a continuum from autonomous technology development to technology commercialization to asking questions of technology-use ethics and national and international policy. He has published more than 60 articles in academic journals and more than 100 peer-reviewed conference papers. Straub serves on multiple editorial boards and conference committees. He is also the lead inventor on two U.S. patents and a member of multiple technical societies.

